Playing Data - Privacy Policies on the Harp
| Playing Data - Privacy Policies on the Harp | |
|---|---|
| Name | Playing Data - Privacy Policies on the Harp |
| Location | Het Wilde Weg |
| Date | 2024/07/16-2024/07/21 |
| Time | 10:00—13:00 |
| PeopleOrganisations | Linden |
| Type | HDSC2024 |
| Web | Yes |
| No | |
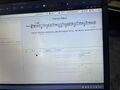
For a while now I've been working on different strategies to make data privacy policies more accessible , especially to a younger and non tech-professional audience. The starting point for the workshop that I would like to give during the summer camp is an interactive installation work, for which I converted the Google data privacy policy to music sheet notation, specifically Veeh-harp notation. The latter was very important for the nature of the concept, since it is an instrument that can be played by people who can't read chords or traditional Western music sheets. Through playing this and other privacy policies, which written out are seemingly endless and often intentionally designed to be intransparent, I want to help people to engage with data privacy in a fun and playful manner. I am beyond curious about the participants realisations of my workshop idea and their perspectives . I suggest that the children bring in their own cryptic messages, or generally texts or content from the internet that at first glance seemed intransparent or confusing. I am also planning on providing such material if nothing comes to mind. Lastly the participants can layout and individually decorate their music sheets, and in the end perform their generated musical pieces. The conversion isn't so much about a transfer of information that is as accurate as possible, more so about engaging closely with information, that is often overlooked and rarely questioned; the layout of the music sheets with the lyrics written on them to follow along further deepens this.
- duration: around 1-2 hours, pretty flexible depending on how detailed and long the cryptified and converted text input is
- number of participants: ideally 5, since there will be five harps, but maximum 10 (2 people per instrument)
- materials / tools: 5 harps , printer that can print A3 !very important!, laptops/PCs with good i!nternet connection! and firefox or chrome installed , min. five ideally if not possible less will do, pens, stickers maybe and drawing tools for decoration the music sheets, maybe stands for the instruments or something to safely lean them against
- what do participants need to prepare: bring their laptop if available and possible, with chrome or firefox, think about whether they've stumbled upon some data privacy policy that they've impatiently agreed to and be mindful about that-ideally bring this in, alternatively some other piece of text related to technology (manual, instruction, code, error) that they found hard or annoyingly confusing to understand
software used/coversion process:
- data privacy policies are often quite long already and encrypting them in their entirety can make them endless, very difficult to render and cause the software to crash, so I'd recommend choosing a few phrases or a paragraph for the beginning
- text to abc-notation , "Solfa Cipher" http://Solfa-Co.de/secrets © 2013 - Revised: 2023 - cipher{at}solfa-co[dot]de , I'll bring printed out cipher grids which visualize the algorithm this software uses, integrated into this is an abc converter https://github.com/paulrosen/abcjs
- abc to Veeh-harp nonation "Zupfnoter
- music sheet decoration Adobe inDesign or in this workshop analogue tools
playing chords on the harp
- playing and recording song
potential data policies, or other "ineligible data speak" (ones I will provide, regardless of what participants will bring:) )
- Google (Browser)
- Apple ICloud
- Microsoft
- Zoom
- Google Maps
- OpenAI (ChatGPT)
- Online Dispute Resolution Regulation
Linden Derichs: I live in Berlin, on the internet, and a few times during the year in the Alps,
I currently study computer science as well as new media art, specializing in emotional technology, media archeology, queer computational online cultures, digital intimacy as well as instrument building.
I don’t like to share my work as an individual’s creation, I would love for it to be mostly woven into collective subconsciousness rather than exhibited. It is a tool for me to speak fully, to be felt in a mind that makes verbal communication sometimes fail me,. To accept our ghost like being and hold space for the endless misunderstanding that is acting, wanting, and moving forward to all. This is technology to me. making isolation an invitation to a collective experience, making computing a love ballad. In my work, technology is supposed to be ; free, sexy, mystical, sentimental, joyful, romantic, organic, decentralized, sustainable, and deeply queer.